Deploy Microsoft Updates with SCCM – the User-Friendly Way
By Arjan Pater
- 578
- System Center Configuration Manager ,
- 05 Dec
Sometimes, updating computer systems with the latest Microsoft Windows updates and patches is difficult. Users are disrupted during their work. Applications may fail to function properly. Last but not least, the look and feel of the Windows operating system is changed. However, installing the latest (security) updates on a regular basis is more important than ever. Just read this article for example: http://www.bbc.com/news/technology-39901382 and if you’re not up to date with your Microsoft (security) updates, you may want to care about that now.
In this article, I write about an update strategy that I implemented at a customer who was worried about ransomware attacks and the impact these could have for his organization. Ransomeware is software that blocks access to important data, unless a ransom is paid. If all the company data is encrypted it could have a lot of impact. For more information, please check the Wikipedia article about ransomware.
The customer already had a mechanism in place for updating the users’ computer systems. However, it needed some improvement. Some users never shutdown their computer systems at the end of a working day. Thus, they could postpone the system restarts forever as these usually are executed when the computer is rebooted. In these cases, the installation of critical security updates is never completed. This is a bad situation as Windows systems are dependent on a restart to finish the installation of Windows updates. As a result, the customer wanted to make sure that updates are installed, systems rebooted when necessary, and the users informed properly.
The Microsoft updates are downloaded with the Windows Server Updating Services (WSUS) that is integrated within the System Center Configuration Manager (SCCM). Using these mechanisms, updates are distributed to laptops and client computer systems. The Configuration Manager Client as well as the settings that are used are essential for this mechanism.
The behavior of the Configuration Manager Client is controlled by the settings as shown in the screenshots below.
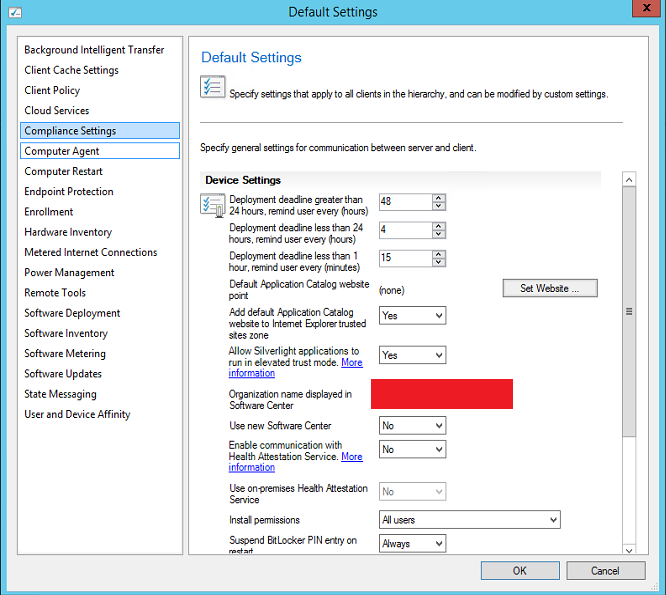
These are the default System Center Client agent settings. These are the default settings.
- If the deployment deadline is greater than 24 hours, then give a reminder to the user every 48 hours.
- If the deployment deadline is less than 24 hours, give the user a reminder the user every 4 hours.
- If the deployment deadline is less than 1 hour, remind the user every 15 minutes.
Now go to the restart options.
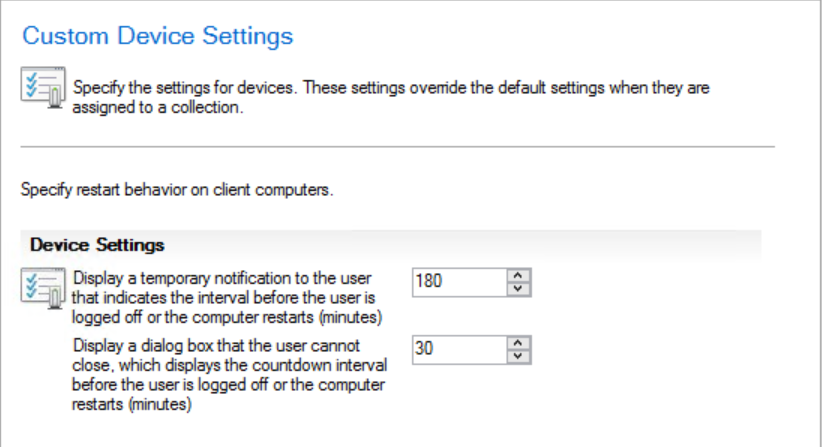
Set these restart options as they fit you best. My customer decided that these settings suits his needs:
- The users are presented with a temporary notification that indicates the interval before the user is logged off or before the computer restarts. In this case: 180 minutes.
- Display a dialog box that the user cannot close which displays the countdown interval before the user is logged off or before the computer restarts. This is set to: 30 minutes.
Everything is set, so that when the Windows security updates are deployed, the settings as configured above will be applied. Let’s do a deployment and see what the user will experience:
Every second Tuesday of the month Microsoft releases new updates. Security updates will be selected for distribution in these weeks. The updates are distributed to a pilot group of users before the they are finally being releases to all company systems. In the screenshot below, the SCCM collections are shown.
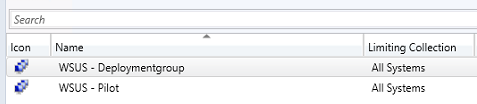
I leave it open how to collect the members for the computer collections. However, I suggest using WMI queries or maybe direct membership for pilot purposes. Just make sure the collections are filled with the computer systems who should receive the Windows updates. In the Software Update Groups, I made two groups for the two system collections. See the screenshot below.
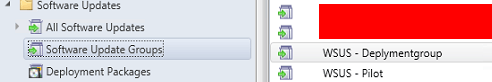
Now it’s possible to deploy the Software Update Groups to the collections.
- Deploy button
- Select the update group and press deploy and follow the Wizard.
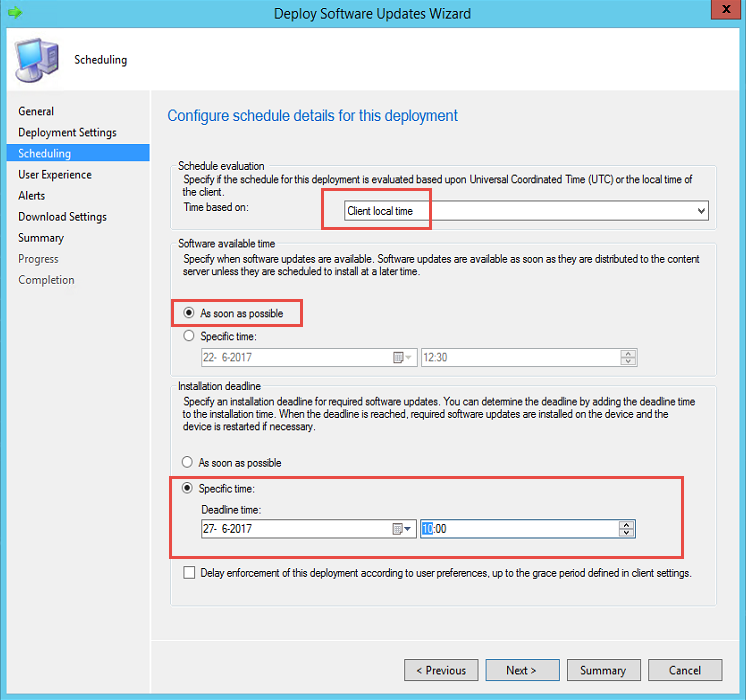
- Set a deadline. In my case the customer decided that a three-day deadline is enough.
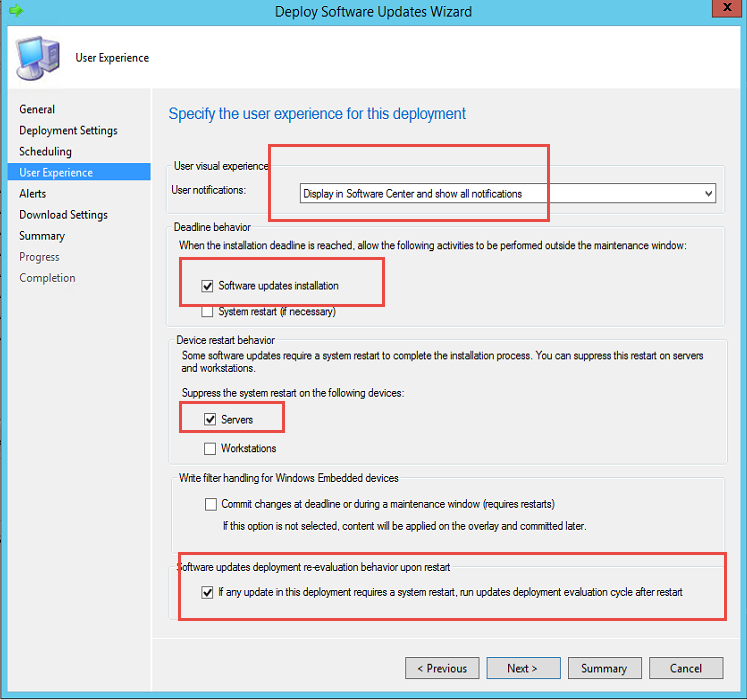
- I choose the options as above when deploying updates. I am following the company guidelines as much as possible, but maybe other options are more suited for your company.
As soon as the deployment of the new Microsoft updates is running, the users have three days’ time to install the updates themselves (we set this deadline in the wizard). The user is informed that there are updates available. See the screenshot below.
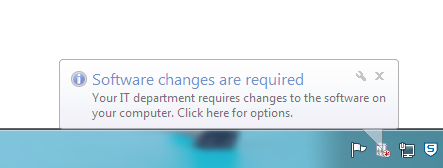
Users can ignore these messages for three days. If they decide to click on it, the screen as shown below opens.
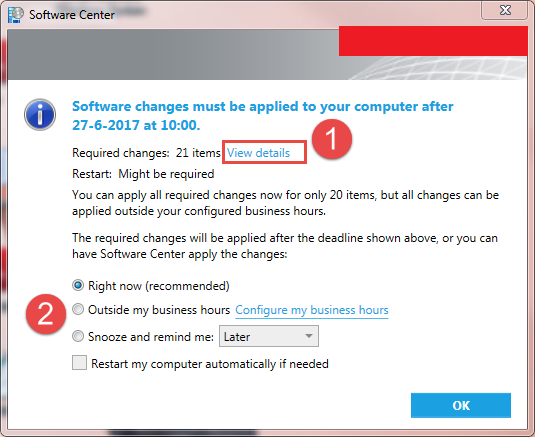
- If “view details” is clicked, the user sees what kind of Microsoft updates are available.
- Here, the user can decide when to install the Microsoft updates available.
From my experience, most users go for the option: “Snooze and remind met later.”
However, the deadline is reached after three days. The updates are downloaded in the SCCM cache and then installed in the system. Now the system needs to be restarted and the user is presented with the popup as shown below.
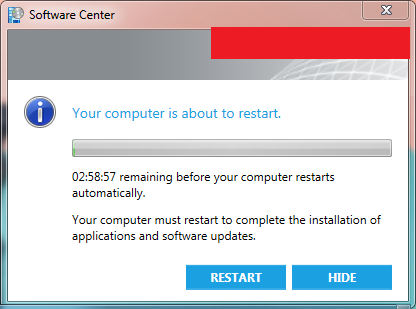
For the user, it’s possible to hide this popup window. Here you see the 180 minutes countdown that we set in the System Center Agent Custom Device Settings.
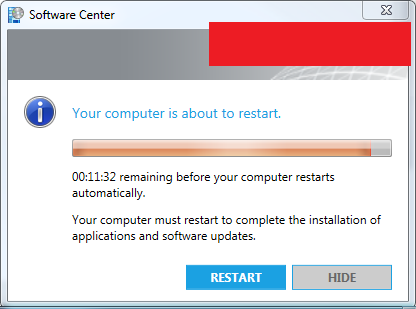
Users can’t hide this message anymore. This happens in the last 30 minutes of the 180 minutes countdown. I configured this in the System Center Agent Custom Device Settings. All the programs that are open are in background now and there is no excuse for the users to say they have not been informed or lost work due to an unexpected restart. The users could even influence the installation and restart their own computer systems themselves. The only thing they can’t do anymore is postpone the installation of the Windows updates forever.
If the counter reaches 00:00:00 the computer is being restarted and the installation of the Windows security updates is completed. With this behavior, the computer systems stay up to date with the latest Microsoft updates and the customer is more protected against ransomware.